Photoshop
Source click here
A PhD student at the University of Michigan that Thomas Knoll, in 1987 wrote a program on a Macintosh Plus to display grayscale images on a monochrome display. Together with his brother John Knoll who are also employees of Industrial Light & Magic, turn it into an image editor program. In 1988 the two sisters with the name change ImagePro. After that year, Thomas renamed his program into Photoshop and work in the short term with the scanner's manufacturer Barneyscan to distribute copies of the program with a slide scanner; "A total of about 200 copies of Photoshop has been sent".
During that time, John traveled to Silicon Valley in California and gave a demonstration of the program to engineers at Apple Computer Inc. and Russell Brown, art director at Adobe. The second demonstration was successful, and Adobe decided to purchase the license to distribute in September 1988. While John worked on plug-ins in California, Thomas remained in Ann Arbor writing program code. Photoshop 1.0 was released in 1990 for Macintosh.
Source click here
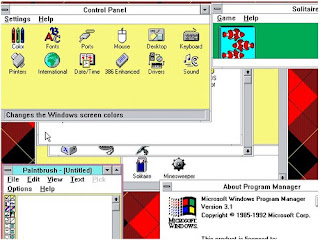
Microsoft Windows eventually achieve significant success when stepping version 3.0 which was released in 1990. In addition to offering increased capabilities to Windows applications, Windows 3.0 is also able to allow users to run multiple MS-DOS applications simultaneously (multitasking), because in this version has introduced virtual memory. This version is precisely what makes the IBM PC and compatibles serious challenger to the Apple Macintosh. This is due to improved performance graphics processing at the time (with the graphics card Video Graphics Array (VGA)), and also protected mode / 386 Enhanced mode that allows Windows applications to use more memory in a way that is much easier compared to what offered by MS-DOS.
Windows 3.0 can run in three modes, namely real mode, standard mode, and 386 Enhanced mode, and is compatible with Intel family of processors from Intel 8086/8088, 80286, to 80386 Windows 3.0 will try to detect which mode will used, although the user can force Windows to work in a certain mode using certain switches when running
win / r: force Windows to run in real mode
win / s: forcing Windows to run in standard mode
win / 3: forcing Windows to run in 386 Enhanced mode.
Version 3.0 is also the first version of Windows that runs in protected mode, although the 386 enhanced mode kernel is an enhanced version of the protected mode kernel in Windows / 386.
Because of the backward compatibility feature, Windows 3.0 applications must be compiled using 16-bit environment, so that did not use the capabilities of the Intel 80386 microprocessor, which is actually a 32-bit processor.
Windows 3.0 also comes in a version of "multimedia", called Windows 3.0 with Multimedia Extensions 1.0, which was released a few months later. This version is bundled with the existence of "multimedia upgrade kits", consisting of a CD-ROM drive and a sound card, like Creative Labs Sound Blaster Pro. This version is the pioneer of all the multimedia features present in later versions of Windows, such as Windows 3.1 and Windows for Workgroups, and become part of the Microsoft Multimedia PC specification.
The features mentioned above and support the application software market growing 3.0 makes Windows very successful in the market. Noted, in the two years prior to the release version of Windows 3.1, Windows 3.0 sold 10 million copies. Finally, Windows 3.0 was a major source of income of Microsoft, and Microsoft did make some revisions to the original plan.
The benefits of the Internet for daily life
- Internet as a source of information on any subject would be very helpful people's lives. For those who work in education, the field of literacy, or the arts, can find a variety of information from internet.Misalnya, if there is a teacher or professor who will give the subject matter and want to find more information, they can use the internet. Not only in terms of employment, anyone can find information on just about anything, for example, to find articles about disease information, information entertainment venues, etc.
- The existence of the Internet can facilitate or expedite a job. For example, there is a data from one office to be delivered to another office, this submission can use the media electronic mail (email) that would use the internet.
- In terms of relationships, the internet also has a very large role. Many forums and social networks today that can help anyone to add the association. It is also one of the benefits of the Internet for the public. The benefits of social networking is also not just add to the association, but also strengthen the friendship and make our practice to socialize better.
- The advantages of this type of business is you do not need to bother renting land / shop to sell. You just have to prepare the goods for sale, promote it, and then just wait for the buyer to contact Anda.Anda can sell just about anything over the Internet, ranging from fashion, food, services, or even sell the house.
- Therein lies the benefit of social networking on the Internet. You can use any social networking to promote, or even create a personal site that contains your efforts.
Those are some benefits of the Internet for the public. Internet simplifies life, both in terms of employment, socialization, even in terms of business.
Windows 2.1x
Furthermore, two new versions were released, namely Windows / 286 2.1 and Windows / 386 2.1. As with previous versions of Windows, Windows / 286 uses real-mode memory model, but was the first version to support the High Memory Area (HMA). Windows / 386 2.1 has a kernel running in protected mode with emulation Expanded Memory Specification (EMS) standard Lotus-Intel-Microsoft (LIM), the predecessor specifications Extended Memory Specification (XMS) which would finally change the topology of computing at the IBM PC. All Windows and DOS-based application when it was run in real mode, running over the protected mode kernel by using the virtual 8086 mode, which is a new feature which is owned by Intel 80386 2:03 Version 3.0 and later versions getting demands from Apple because the version 2.1 this has the appearance of a window in cascade mode (overlap), in addition to several features of the Apple Macintosh operating system that is "emulated" by Windows, is the main problem to see / look and feel. Judge William Schwarzer ended up canceling all 189 charges, except the nine charges filed by Apple against Microsoft on January 5, 1989.
Windows 2.x
Microsoft Windows eventually obtained a significant increase when Aldus PageMaker appeared in versions for Windows, which previously could only run on the Macintosh. Some computer historians date this, the emergence of a significant application that behavior other than by Microsoft as the early success of Windows. Windows version 2.0x using real-mode memory model, which is only able to access the memory to 1 megabyte. In such configurations, Windows can run applications more multitasking, sort DESQview, which runs in protected mode offered by the Intel 80286.
Windows 1.0
The first version of Microsoft Windows, called Windows 1.0, released on 20 November 1985. This version has many shortcomings in some functionality, making it less popular in the market. At first Windows version 1.0 is going to be named by the Interface Manager, but Rowland Hanson, the head of marketing at Microsoft Corporation, Microsoft assured officials that the name "Windows" will be "lure" customers. Windows 1.0 is not a complete operating system, but only extending the capabilities of MS-DOS to a graphical interface enhancements. In addition, Windows 1.0 also has the same problems and weaknesses that are owned by MS-DOS.
Furthermore, Apple is demanding Microsoft makes Microsoft is limiting his ability. For example, the windows in Windows 1.0 can only be displayed on the screen in "tile" only, so that the window can not overwrite each other. In addition, there is no such place that is used to save a file before it is deleted (Recycle Bin), because Apple believes that they have the rights to that paradigm. Microsoft would then throw the limitation of Windows by signing a license agreement with Apple.
Continuation of Windows 1.0 click here
The first version of Microsoft Windows, called Windows 1.0, released on 20 November 1985. This version has many shortcomings in some functionality, making it less popular in the market. At first Windows version 1.0 is going to be named by the Interface Manager, but Rowland Hanson, the head of marketing at Microsoft Corporation, Microsoft assured officials that the name "Windows" will be "lure" customers. Windows 1.0 is not a complete operating system, but only extending the capabilities of MS-DOS to a graphical interface enhancements. In addition, Windows 1.0 also has the same problems and weaknesses that are owned by MS-DOS.
Furthermore, Apple is demanding Microsoft makes Microsoft is limiting his ability. For example, the windows in Windows 1.0 can only be displayed on the screen in "tile" only, so that the window can not overwrite each other. In addition, there is no such place that is used to save a file before it is deleted (Recycle Bin), because Apple believes that they have the rights to that paradigm. Microsoft would then throw the limitation of Windows by signing a license agreement with Apple.
Continuation of Windows 1.0 click here
What's cybercrime
Cyber Crime is a new form of crime using the internet as a medium for committing crime ith the advent of the internet era. Every criminal activities committed on the internet or through the Internet, commonly referred to as Internet crime.
Types of cyber crime and violations are very diverse as a result of the application of technology. Cyber crime can be wiretapping and misuse of the information or data in electronic form and transferred electronically, theft of electronic data, pornography, abuse of a child as an object against the judiciary, fraud memalui internet, gambling diinternet, vandalism website, in addition to the heaping system through a virus, Trojan horse , signal grounding and others.
Who cybercrimes?
We need to know the perpetrators of cybercrime are those who have high expertise in computer science, perpetrators of cybercrime is generally controlled algorithms and computer programming fatherly create a script / code malware, they can analyze the workings of computer systems and networks, and is able to find loopholes pasa system will then use the weakness to be entered so that crimes such as theft of data can be successfully carried out.
Types of Cybercrime
There are several types of crimes on cyber crime can be classified based on the activities done as described below are summarized from various sources.
- unauthorized Aces => Is a crime that occurs when someone enters or infiltrate into a computer network system illegally, without permission, or without the knowledge of the owner of the computer network system is entered. Examples of these crimes are Probing and port.
- illegal Contents => A crime that is done by entering data or information into the Internet about something improper, unethical, and can be regarded as unlawful or disturb the public order, for example, is the spread of pornography or untrue reports.
- The spread of the virus intentionally => Spread of the virus is generally performed by using an email. Often people are exposed to the virus e-mail system is not aware of this. The virus is then transmitted to another place via email.
- Cyber Espionage, Sabotage, and Extortion => Cyber Espionage is a crime by way of utilizing the Internet to conduct espionage against other parties, by entering into the target computer network system. Sabotage and Extortion is the type of crime committed by creating a disturbance, destruction or the destruction of the data, computer programs or computer network system connected to the Internet.
- Carding => Carding is a crime that is made to steal credit card numbers belonging to others and used in commercial transactions on the Internet.
- Hacking and Cracker => The term hacker refers to someone who has a great interest in learning the details of computer systems and how to improve capabilities. Cracking activity on the Internet has a very wide scope, ranging from hijacking an account belonging to someone else, piracy websites, probing, spread the virus, to incapacitate the target. Last actions called DoS (Denial of Service). Dos attack is an attack aimed at paralyzing the target (hangs, crashes) therefore can not provide the service.
- Cybersquatting and typosquatting => Cybersquatting is a crime committed by registering domain names the company of others and then trying to sell it to the company with a more expensive price. The typosquatting is a crime to make a play domain is a domain that is similar to the domain name of another person.
- Cyber Terrorism => Measures cybercrime including cyber terrorism if it threatens the government or citizens, including cracking to the government or military.